Download PDF
Download page Recommended Approach.
Recommended Approach
In general, several methods should be used to predict a range of breach sizes and failure times for each failure mode/hydrologic event. It is recommended that the modeler select several regression equations to estimate breach parameter values. Care must be taken when selecting regression equations, such that the equations are appropriate for the dam being investigated. Regression equations that have been used for earthen, zoned earth, earth with a clay core, and rockfill dams are: Froehlich (1995a), Froehlich (2008), MacDonald and Langridge-Monopolis (1984), Von Thun and Gillette (1990), and Xu and Zhang (2009). If the dam under investigation is outside the range of data used in the development of the regression equations, resulting breach parameter estimates should be scrutinized closely for reasonableness.
In addition to the regression equations, physically based computer models should also be utilized if appropriate for the level of study (NWS-BREACH, WinDAM, and HR-BREACH models are currently recommended). Whenever possible, geotechnical analyses of the dam should be used to assist in estimating the breach parameters (i.e. side slopes of the breach), or at least used as a qualitative assessment of the estimates. Additionally, breach parameter estimates should be compared to the government agency ranges provided in Table 14-3. If values are outside the recommended ranges, those estimates may need to be adjusted, unless there is compelling physical evidence that the values are appropriate. This will lead to a range of values for the breach size and failure times. A sensitivity analysis of breach parameters and times should be performed by running all of the parameter estimates within the HEC-RAS model.
Each set of breach parameters and failure times will produce a different outflow hydrograph. However, once these hydrographs are routed downstream, they will tend to converge towards each other. There are two main reasons for this convergence: (1) the total volume of water in each of the different hydrographs is basically the same (being the stored water behind the dam at the time of failure, plus whatever inflow occurs); (2) as the hydrographs move downstream, a sharp hydrograph will attenuate much more quickly than a flat hydrograph. Hydrographs from different assumed breach parameters can converge to produce similar peak flow and stage in a surprisingly short distance. An example flow versus time plot from a study performed with HEC-RAS is shown in the figure below. However these differences could be huge for Loss of Life calculations if a population at risk is immediately downstream of the dam.
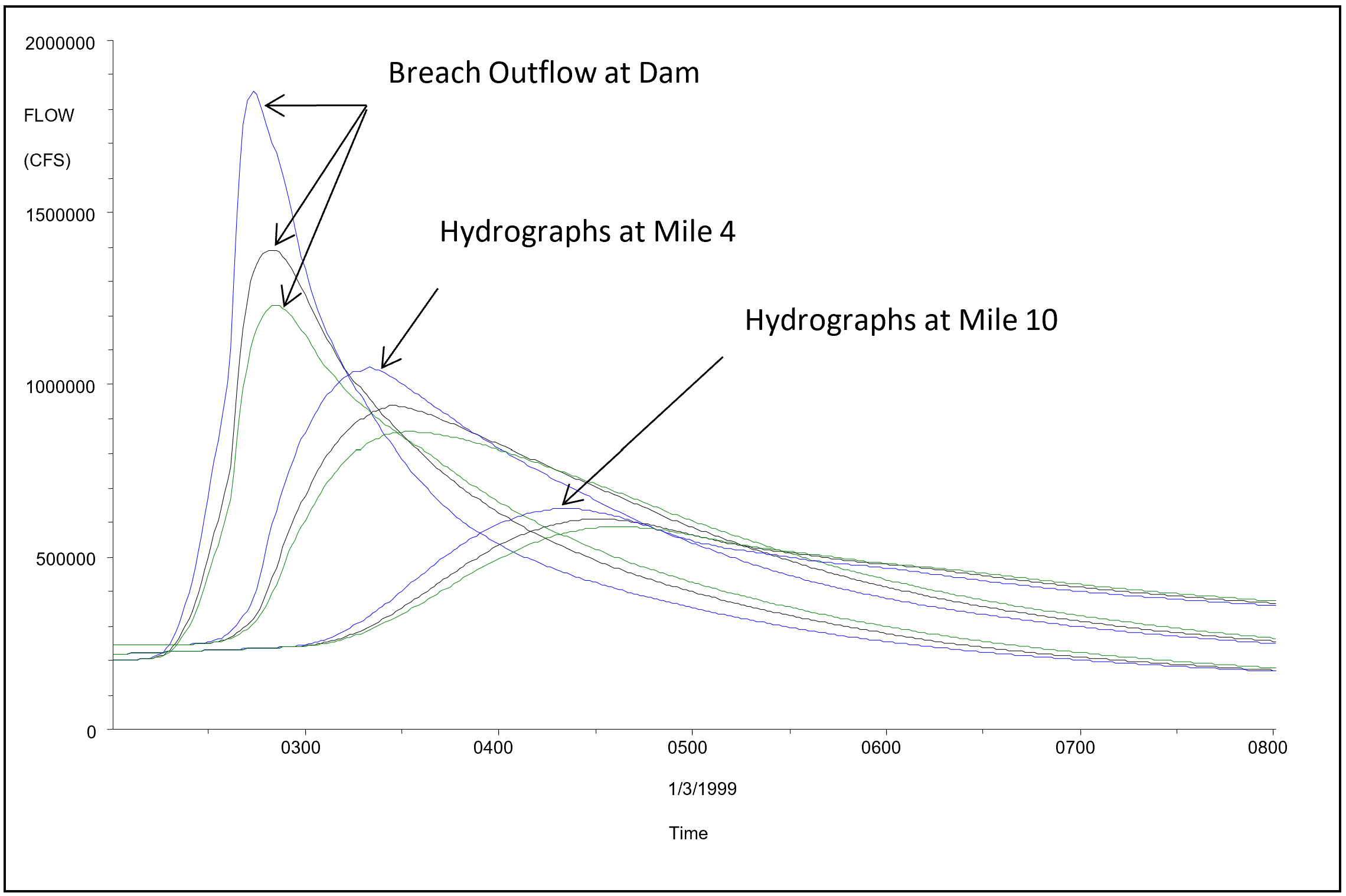
In the example shown in the figure above, three different sets of breach parameters were used for the same model. The hydrographs coming out of the dam are very different in magnitude of peak flow, but they have the same volume of water. In this example, as the hydrographs move downstream they have substantially converged within four miles and are almost the same peak flow by mile 10. The rate at which the hydrographs will converge is dependent on many factors: steepness in the rise of the outflow hydrograph, volume of the outflow hydrograph, slope of the downstream reach, roughness of the downstream reach, available storage in the downstream floodplain, etc… The user will need to route all of the breach outflow hydrographs downstream through the entire study area in order to fully evaluate the affect of the breach parameters on the resulting flood hydrographs and inundation levels.
For a risk assessment study, the user must select the set of breach parameters that are considered to be most likely for each event/pool elevation. This will require engineering judgment. If all of the breach estimates, for a given event/pool elevation, end up converging to the same flow and stage before getting to any population at risk and potential damage areas, then the selection of a final set of breach parameters should not affect the computations and a simple mean value should be used. However, if the various sets of breach parameters produce significantly different flow and stage values at downstream locations (population at risk locations and potential damage zones), then engineering judgment will need to be used to pick a set of values that are considered most likely. Conservatively high or low values should not be used, as this will bias the overall results.
Once a final set of breach parameters is selected for a given event/failure mode, the computed peak outflow from the breach can be compared to some of the peak flow equations as a check of reasonableness. Keep in mind the limitations of the peak flow equations, as discussed in the Peak Flow Regression Equations section above.
Another check for reasonableness should be done by evaluating the breach flow and velocities through the breach, during the breach formation process. This can be accomplished by reviewing the detailed output for the inline structure (Dam) and reviewing the flow rate and velocities going through the breach. This output is provided on the HEC-RAS detailed output table for the Inline Structure. There are two things to check for here:
- if the model reaches the full breach development time and size, and there are still very high flow rates and velocities going through the breach, then this is a sign that either your breach is too small, or your development time is to short (unless there are some physical constraints limiting the size of the breach).
- if the flow rate and the velocities through the breach become very small before the breach has reached its full size and development time, then this is an indicator that your breach size may be too large, or your breach time may be too long. Additional factors affecting this could be your breach progression curve and the hydraulic coefficients (weir and piping) you used. When you get into the situation described above in either scenario 1 or 2, the breach size and development time should be re-evaluated to improve the estimates for that particular structure.
The level of effort in estimating breach parameters should be consistent with the type of risk assessment. In general, the level of effort and detail will increase from Type 1 (Low Hazard Potential) through Type 3 (High Hazard Potential). For Type 1 analyses a basic estimate of breach parameters consistent with the range of values in Table 14-3 could be appropriate. Type 2 (Significant Hazard Potential) and Type 3 analyses will typically require a greater level of detail and accuracy incorporating most if not all of the methods provided in this Section.